NorthStar Privilege Tracking
Privilege Tracking Simplified
The concept of aggregating data to understand privileged access is typically a labor-intensive, complicated, time consuming and expensive process that tends to yield unquestionable results.
NorthStar Privilege Tracking does all the heavy lifting for you.
NorthStar gives you the ability to aggregate and analyze privileges across your various business and IT platforms by leveraging data that already exists in the tools and applications deployed in your environment. It provides visibility into all of the user privileges and entitlements across your so you can identify risks, spot issues and make the right decisions to improve the effectiveness of your security posture.
Privileges Meet Continuous Monitoring
Long gone are of the cumbersome tasks of manually gathering and analyzing data from disparate sources. NorthStar’s comprehensive data, analytics and reports are refreshed through its automated processes, giving you the ability to track what people have access to and the changes in those privileges over time. This validates remediation is taking place in a timely manner and allows you to identify new privileges that appear in your environment.
Where NorthStar Shines
NorthStar is unique in the market as one of the only solutions to provide unified reporting across all levels of access in a single repository. Whether it is server privilege, file share, application, or even a badge to facility, all privileges – both physical and virtual – can be tracked and reported on in a single pane of glass.
When the NorthStar Privilege Tracking module is used with the Asset Tracking module, you gain valuable information on each of the resources in your environment and can automatically generate new exposure metrics based on those privileges for things such as the number of elevated accounts on a system, or the existence of an account that doesn’t have a corresponding approval.
Checks and Balances
Identity and access management solutions will give you a picture of what should be in place, whereas NorthStar focuses on what is truly in place making it the perfect compliment to your IAM solution.
By tracking people and their associated user accounts, where those accounts have privileged access, and what they are associated with in near real-time, NorthStar reporting and visualizations provide you with the actionable information you need to efficiently deal with the complexities of user access management, insider threats and compliance requirements.
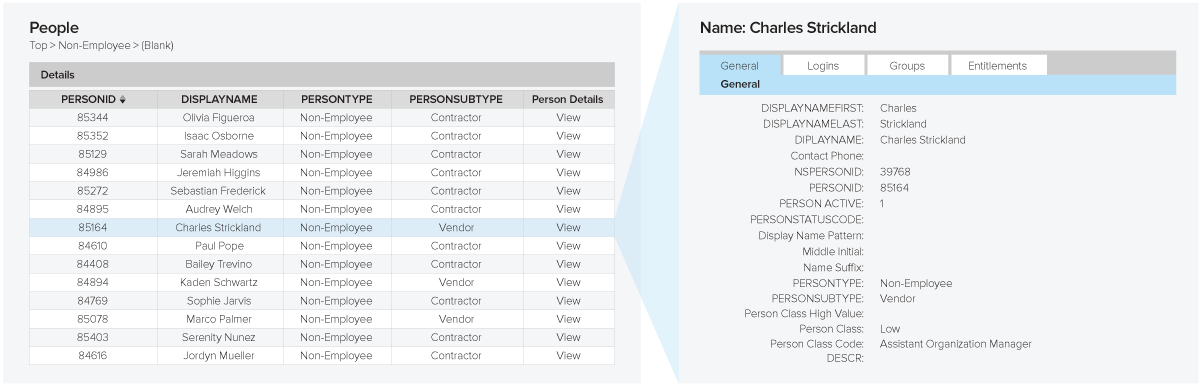
Beyond each detailed list, each has a MASTER record with the consolidated that is pulled from multiple sources across your environment that can be viewed.
When viewing a person’s MASTER record, you can view the Login IDs they own, what Groups they are a part of, and what Entitlements they have to the different Resources across your environment. This eases the top pain points of User Access Reviews.
NorthStar
Know what you’re protecting!